Background
For an upcoming episode of McAfee’s Hackable podcast, I was provided with a Furbo – a dog food tossing device, for a security review.
Equipped with a 160 degree High Definition camera and night vision capabilities, Furbo is a dog camera capable of tossing food with a swipe of a button through your phone. Furbo was featured on the media quite a few times, such as on New York Times, Tech Crunch and also recently on the Ellen Degeneres Show, where they gave out Furbos to the audience for Christmas Giveaways.

What happens behind the scenes
Furbo uses Bluetooth for the initial device setup, and uses Real Time Streaming Protocol (RTSP) – RFC 2326 for video streaming. Video streams are sent to IP addresses in multiple regions, and every photo taken by the Smart Dog Alerts feature is uploaded to an Amazon S3 bucket.
Furbo’s mobile App fetches your photos directly from their cloud service, once you browse to the main page. This will eventually populate the app’s timeline, which is where all the events that occurred that day go.
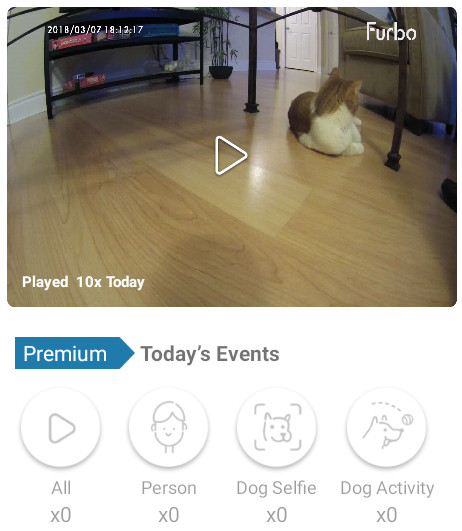
Vulnerability #1 – Daily Events API without Authentication
The problem lies in one of the API calls the mobile application does, which is to receive the events of the day the moment you open the app. Events are photos/moments taken by the device, which are later categorized by either ‘Person’, ‘Dog Selfie’ and ‘Dog Activity’.
The retrieval of these photos is done by API call to Furbo’s event processing servers. The server, in return, would respond with a JSON payload. This JSON includes all of today’s events, determined by a LocalTime parameter, with the current date as its value, which is sent along with the request. The response would then contain 3 different keys: PersonDetected, DogMoveAbove10secs and Selfie.
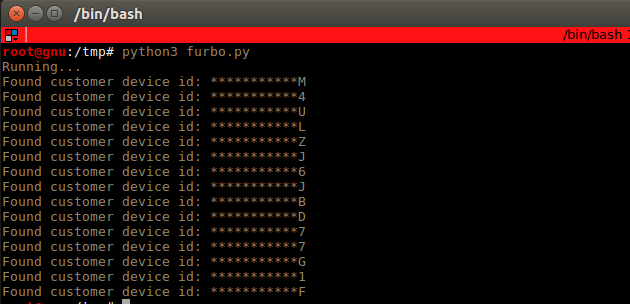
Although Furbo implemented some security measures, for example, ensuring the transmission of data is done over HTTPS, The APIs rely on the “randomness” of the MAC address passed as a URL paramter. Furbo is equipped with a camera made by the Taiwanese camera manufacturer called Chicony Electronics, their addresses are prefixed with B0:C0:90, so it should be trivial to brute force.
By generating a dictionary of MAC addresses and brute forcing the remainder MAC address, it was possible to access other accounts pictures, since there’s no real Device to Account association.
The following code can be used to generate random MAC addresses:
>>> for _ in range(200): print "%s:%02x:%02x:%02x" %('B0:C0:90', random.randint(0, 255), random.randint(0, 255), random.randint(0, 255))
...
B0:C0:90:74:c5:d6
B0:C0:90:02:64:85
B0:C0:90:ab:3e:a4
B0:C0:90:00:1c:5f
B0:C0:90:bf:fc:e3
B0:C0:90:94:d7:8a
B0:C0:90:5c:b3:86
B0:C0:90:b0:57:c7
B0:C0:90:ca:37:b0Collecting Furbo devices to attack
Vulnerability #2 – Unauthenticated Treat Tossing Audio Upload
Snack Call is another feature of Furbo, which calls your dog before the food gets tossed. The feature lets you either record a 6 seconds message or use the default built in sound, which gets played when you swipe the little food icon on the App.
This feature, in the same fashion as the previous flaw, used an API to upload the audio and then in return a signed S3 link was provided.
I did not have enough time to further explore this feature due to the fast reaction of the company in blocking the feature once I reported it. However, it is likely that the audio upload function was also vulnerable.
Theoretically, I could have uploaded a sound file of my own to other people’s Furbo accounts.
Vulnerability #3 – Zero Click Account Takeover
Upon a reset password request, the response from the website contained a suspicious token, which I noted down.
After some experiments, I realized the token returned is the same code that constructs the unique password change link.
HTTP/1.1 200 OK
Date: Sat, 10 Mar 2018 13:33:58 GMT
Content-Type: application/json
Content-Length: 69
Connection: close
Server: Werkzeug/0.12.2 Python/3.5.2
{"Message":"IkhQTFRaU[redacted]VjIEly2XUWdVMAh8"}In this case, all an attacker needs to do is browse to: https://site.com/reset/IkhQTFRaU[redacted]VjIEly2XUWdVMAh8 and reset the victim’s password.
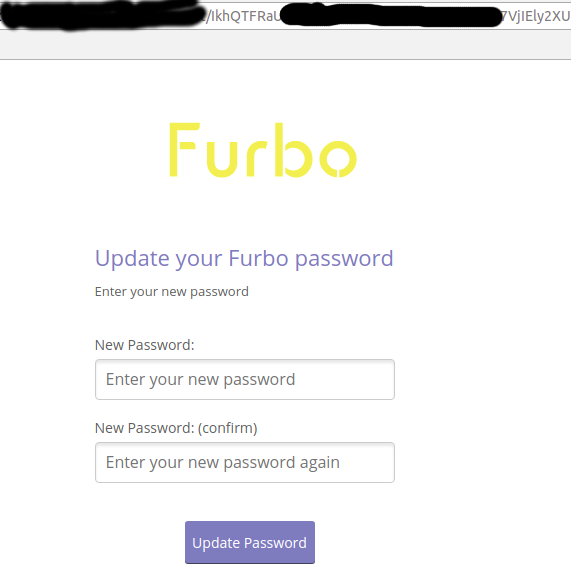
This leads to a complete zero click account takeover.
Account Takeover Demo
Disclosure
Tomofun, the company behind Furbo, asked for a proof exploit and provided me with an account they own for me to try. Here is their office view from their Furbo after a successful exploitation:

All issues were addressed in a timely manner.
TL;DR
Lack of authorization checks, predictable device IDs used in APIs and a broken password reset mechanism flaws allowed full remote access to all of any Furbo account without user interaction required.
